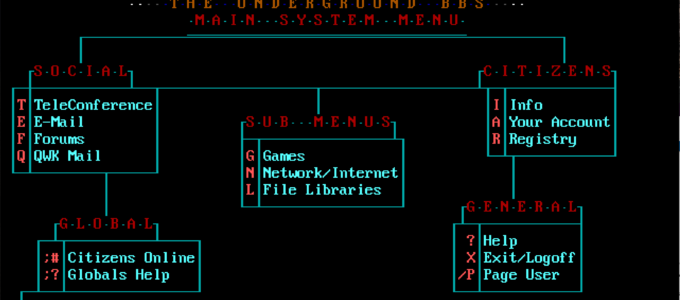
This is our world now… the world of the electron and the switch, the beauty of the baud.The Mentor (http://phrack.org/issues/7/3.html) When dial-up ruled There was a time that some of us can still remember. A time before fast networks ruled the industry. When connection speeds over 1mbps were blazing fast, and most of us lived…
My Sysadmin Story
Note: This story was originally written for Red Hat’s Enable Sysadmin blog. We’ve all got a story, right? Our lives could be laid out like a script for a movie, or in the chapters of a novel. I don’t know if anyone would read mine, but to the right audience, it might sound familiar, or…
What My Family Thinks I Do For a Living
Note: This was originally written for Red Hat’s Enable Sysadmin Blog, https://www.redhat.com/sysadmin The job title “System Administrator” is sometimes vague within the industry. Some sysadmins are responsible for a wide swath of devices, from desktops, to servers, to printers, to air conditioning units. So, sometimes when you tell another IT professional that you’re a sysadmin,…
How to Validate Security by Scanning All The Things
Note: This article was originally published on Red Hat’s Enable Sysadmin blog, https://www.redhat.com/sysadmin In parts one and two of this series, I walked you through hardening your system by identifying unneeded services, then segmenting and firewalling. Now that you’re all locked down, let’s talk about how we might validate that all of that hard work…
Defense in Depth
Note: This was originally posted on Red Hat’s Enable Sysadmin blog. https://www.redhat.com/sysadmin This is the next step in my series on hardening and network security. Please check out the previous article on Lowering your Attack Surface by Disabling Unnecessary Services. Flat Networks There was a time when all networks were flat. A flat network is…
How to Lower Your Attack Surface
Note: This was originally posted on Red Hat’s Enable Sysadmin blog. https://www.redhat.com/sysadmin Linux systems are complicated things. Out of the box, every distribution includes a number of services meant to help you get things up and running. Some distributions enable less services by default, some enable more. The difference is in convenience. Some distributions are…
Geeking Outside The Office
This was originally written for Red Hat’s Enable Sysadmin. Enjoy!Nate Sysadmins have plush easy desk jobs, right? We get to sit in a nice climate controlled office, and type away in our terminals, never really forced to exert ourselves. It might look that way, and as I write this during a heat wave here in…
The Day The RHV Manager Went Away…
This is an article I originally wrote for Red Hat’s Enable Sysadmin. Nate Late on a tuesday afternoon, I had somewhere to be after work, that made driving all the way home and then back again a waste of time. So I was in my office late, killing some time, getting a little work done,…
Sysadmin Appreciation Day
This is an article I wrote for Red Hat’s Enable Sysadmin for Sysadmin Appreciation Day 2019. Enhoy!Nate Sysadmin appreciation day is coming, on July 26th you’ll have a chance to thank one of the least thanked people in your life, your local Sysadmin. In today’s connected world, it’s likely that you rely on a sysadmin…
Locking down sshd
SSH, or Secure SHell, is the way in which a modern linux system is managed. Most experienced sysadmins love the direct access and power they get from being able to securely connect to a shell on their systems with relative ease. SSH replaced Telnet somewhere in the 90’s as the remote access protocol of choice,…
-
Recent Posts
Recent Comments
- Episode 112b – AWS down again, Facemeta, and Android users cant dial 911! – Iron Sysadmin Podcast on Virtual Reality, Online Worlds, and Metaverses
- Untangling my life from the Google ecosystem - Undrblog on Nextcloud, in a container, in a bucket
- Untangling my life from the Google ecosystem - Undrblog on Getting my digital life back from Google Photos
- Nextcloud, in a container, in a bucket - Undrblog on Getting my digital life back from Google Photos
- Getting my digital life back from Google Photos - Undrblog on Untangling my life from the Google ecosystem
Archives
- July 2023
- November 2022
- October 2022
- December 2021
- August 2021
- January 2021
- December 2020
- September 2020
- July 2020
- March 2020
- February 2020
- January 2020
- October 2019
- August 2019
- June 2019
- January 2019
- December 2018
- June 2018
- July 2017
- June 2017
- April 2017
- March 2017
- December 2016
- October 2016
- June 2016
- September 2015
- July 2014
- December 2013
- August 2013
- July 2013
- June 2013
- April 2013
- March 2013
- January 2013
- December 2012
- October 2012
- September 2012
- August 2012
- July 2012
- June 2012
- February 2012
- January 2012
- November 2011
- October 2011
- August 2011
- July 2011
- June 2011
- May 2011
- April 2011
- March 2011
- February 2011
- January 2011
- October 2010
- September 2010
- August 2010
- June 2010
- May 2010
- April 2010
- February 2010
- January 2010
- December 2009
- October 2009
- September 2009
- August 2009
- June 2009
- May 2009
- April 2009
- March 2009
- February 2009
- January 2009
- December 2008
- November 2008
- October 2008
- August 2008
- July 2008
- June 2008
- February 2008
- January 2008
- December 2007
- November 2007
- October 2007
- September 2007
- August 2007
Categories
Meta