Linux, at its base, is just a kernel, but what does the kernel do without additional packages? The Kernel enables everything, but software that interacts with the kernel is what makes a linux distribution. Every distribution has its own way of handling things. Some focus on stability, as a platform for critical workloads, others on…
Building a Mastodon instance, to vacate birdsite. On RHEL, in Podman.
So, maybe you’ve heard about the Musk take-over of twitter, and maybe you’ve heard about the mass exodus of a large number of users from the old platform. Personally I try not to knee-jerk react to things like this but I haven’t been exceedingly active on twitter lately. I have also long had an interest…
Enabling Unsafe Interrupts for PCI passthrough on RHEL 9
This should be a quick one. I bought some older hardware for my home lab/home services and one of the things I want to do with it is host my plex server on it. Plex benefits from a GPU, it doesn’t have to be a fancy one, but a lower end nvidia GeForce desktop adapter…
Virtual Reality, Online Worlds, and Metaverses
Snow Crash, Ready Player One, The Matrix, these are all cautionary tales of what virtual online worlds might bring to the world. I have been exploring the concept of “The Metaverse” a bit since everybody’s favorite evil android Mark Zuckerberg announced that his company, Facebook, was re-branding to Meta in order to position themselves as…
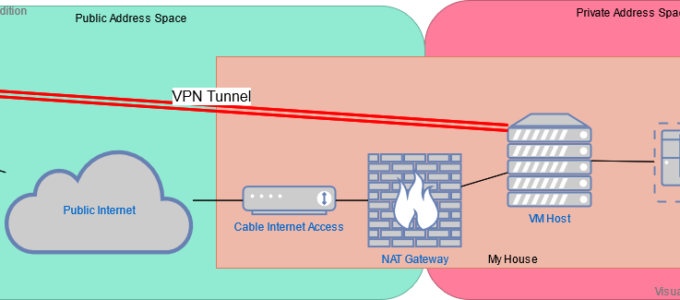
Making those home hosted services available with some help from WireGuard!
So, I have a long history of self-hosting. And let me tell you, self-hosting has gotten harder over the years. There was a point where I ran a linux server in my parents basement. It ran this web site (or a very much older version of it anyway) and a number of other services. In…
Adding a first boot task via systemd
Sometimes You just want to run a task once, the first time a system boots. There are a bunch of ways you could do this, but I was working on trying to solve a specific use case for a customer. In this case, we’d like to run some tasks on the first boot of a…
Nextcloud, in a container, in a bucket
Join me while I build a private cloud document and photo storage solution. Backed by an object store, so you’ll never need to expand your storage as you add files! …
Getting my digital life back from Google Photos
This is the second installment of a series I’m creating on “de-googling”. My goal here is not to eradicate Google from my life, but rather to limit my dependence on them. You can read some back-story in the previous article Untangling my life from the Google ecosystem. My first goal here is to try to…
Untangling my life from the Google ecosystem
Google. It’s become such a part of our lives. Certainly for those of us who are not Apple users. I don’t really have anything against apple exactly. I even ditched my android device for a little over a year and went to an iPhone. It wasn’t terrible, but I just liked the android experience better….
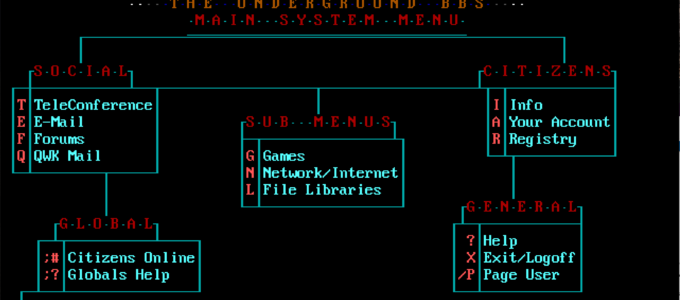
In the Days of Text
This is our world now… the world of the electron and the switch, the beauty of the baud.The Mentor (http://phrack.org/issues/7/3.html) When dial-up ruled There was a time that some of us can still remember. A time before fast networks ruled the industry. When connection speeds over 1mbps were blazing fast, and most of us lived…
-
Recent Posts
Recent Comments
- Episode 112b – AWS down again, Facemeta, and Android users cant dial 911! – Iron Sysadmin Podcast on Virtual Reality, Online Worlds, and Metaverses
- Untangling my life from the Google ecosystem - Undrblog on Nextcloud, in a container, in a bucket
- Untangling my life from the Google ecosystem - Undrblog on Getting my digital life back from Google Photos
- Nextcloud, in a container, in a bucket - Undrblog on Getting my digital life back from Google Photos
- Getting my digital life back from Google Photos - Undrblog on Untangling my life from the Google ecosystem
Archives
- July 2023
- November 2022
- October 2022
- December 2021
- August 2021
- January 2021
- December 2020
- September 2020
- July 2020
- March 2020
- February 2020
- January 2020
- October 2019
- August 2019
- June 2019
- January 2019
- December 2018
- June 2018
- July 2017
- June 2017
- April 2017
- March 2017
- December 2016
- October 2016
- June 2016
- September 2015
- July 2014
- December 2013
- August 2013
- July 2013
- June 2013
- April 2013
- March 2013
- January 2013
- December 2012
- October 2012
- September 2012
- August 2012
- July 2012
- June 2012
- February 2012
- January 2012
- November 2011
- October 2011
- August 2011
- July 2011
- June 2011
- May 2011
- April 2011
- March 2011
- February 2011
- January 2011
- October 2010
- September 2010
- August 2010
- June 2010
- May 2010
- April 2010
- February 2010
- January 2010
- December 2009
- October 2009
- September 2009
- August 2009
- June 2009
- May 2009
- April 2009
- March 2009
- February 2009
- January 2009
- December 2008
- November 2008
- October 2008
- August 2008
- July 2008
- June 2008
- February 2008
- January 2008
- December 2007
- November 2007
- October 2007
- September 2007
- August 2007
Categories
Meta